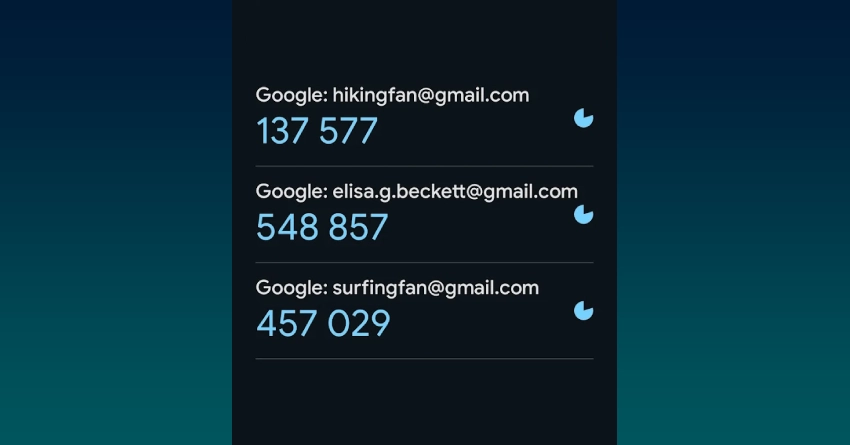
In late 2025, security researchers revealed a new and surprisingly elegant attack technique called Pixnapping — a method that can literally steal what’s on your screen without taking a screenshot or asking for permission. It targets the invisible gap between how Android renders graphics and how the system protects app boundaries.
Even though the name sounds playful, the implications are serious. It proves that sensitive on-screen data — like two-factor authentication codes, recovery phrases, or private messages — can be exposed through the graphics pipeline itself.
What Pixnapping Actually Is
Pixnapping is a side-channel attack. Instead of breaking encryption or bypassing permissions, it listens to the tiny timing signals created while the phone’s GPU and system compositor draw the screen.
When an Android app applies a graphical effect — like a blur or a semi-transparent overlay — the operating system measures and processes millions of pixels. The time it takes to render each pixel can vary depending on its color, brightness, or texture. By monitoring these differences, a malicious app can quietly reconstruct the content underneath.
No screenshots, no root access, no special permissions — yet the attacker still learns what’s displayed.
How the Attack Works
- Trigger the target content: The attacker’s app brings into view a sensitive screen, such as a one-time 2FA code.
- Place a disguised overlay: The app creates a transparent or blurred layer over the same region using Android’s visual APIs.
- Measure rendering behavior: By repeatedly applying and removing the overlay while tracking GPU timings, the attacker detects how each pixel behaves.
- Rebuild the image: Over time, these measurements reveal pixel values, allowing the attacker to reconstruct letters, numbers, or full screenshots.
In research demonstrations, the method was fast enough to extract a six-digit authentication code in under a minute.
Which Devices Are Affected
Tests showed that Pixnapping works on several modern Android phones, including devices from Google and Samsung, running Android versions 13 through 16. Because the technique depends on the core Android rendering system, many other devices may also be at risk.
However, the attacker must first install a malicious app on the target device, so the risk to average users remains moderate rather than immediate.
Why It’s Hard to Fix
The difficulty with Pixnapping lies in where the leak occurs. It doesn’t exploit a bug in an app — it exploits how the operating system and GPU handle graphics. Fixing it requires redesigning parts of the rendering pipeline or introducing timing equalization, which affects performance.
Google released an initial patch in late 2025 that limits risky visual effects, but researchers found that the fix only reduces — not fully prevents — the attack. More comprehensive updates are expected in future Android versions.
How to Protect Yourself
- Keep your device updated: Install Android security patches as soon as they become available.
- Install apps only from trusted sources: Avoid sideloading APKs from unknown websites.
- Check overlay permissions: In settings, review which apps can “draw over other apps” and disable unnecessary ones.
- Use hardware-based authentication: Physical security keys are safer than on-screen codes.
- Be mindful of sensitive screens: Close apps that show private data when not in use.